Introduction
In the first post of this series, we explored how identity has become the new perimeter in a world where users, apps, and data are no longer confined to the corporate network. By putting identity at the centre of your security strategy and enforcing strong, phishing-resistant authentication and Conditional Access you lay the foundation for a robust Zero Trust approach.
But identity is only part of the story. In the world of Zero Trust, identity may be the new perimeter but devices are the frontline. As organisations embrace hybrid work, cloud services, and bring-your-own-device (BYOD) models, the number and diversity of endpoints accessing corporate data has exploded. Laptops, mobiles, tablets, and even personal devices are now gateways to your most sensitive information.
Attackers know this. Compromising a device is often the quickest route to stealing credentials, bypassing security controls, or launching ransomware. That’s why, in a Zero Trust model, it’s not enough to trust a user’s identity alone, you must also verify the health and compliance of the device they’re using, every single time. Zero Trust means never assuming that any device is safe by default. Whether it’s a corporate laptop, a contractor’s tablet, or an employee’s personal phone, every device must continuously prove it meets your security standards before it can access your resources.
This post explores how to put these principles into practice using Microsoft 365, Intune, and Defender for Endpoint. We’ll look at why device security is essential, how to enforce compliance, and practical steps to ensure that only healthy, trusted devices can connect to your environment—no matter where your users are working.
How Intune Supports Device Compliance
Microsoft Intune sits at the heart of device compliance in a Zero Trust strategy. It enables organisations to define, enforce, and monitor security requirements across all devices, whether corporate-owned or BYOD. Here’s how Intune supports device compliance:
- Policy Creation: Define minimum security standards for devices, such as encryption, OS version, password complexity, antivirus status, and whether the device is jailbroken or rooted.
- Automated Enforcement: Intune automatically evaluates enrolled devices against these standards, flagging non-compliant devices.
- Conditional Access Integration: Seamlessly integrates with Microsoft Entra Conditional Access, ensuring only compliant devices can access sensitive apps and data. Non-compliant devices are blocked or restricted until resolved.
- Real-Time Monitoring and Reporting: Dashboards and reports provide visibility across your device estate, helping IT teams identify risks and act quickly.
- Remediation and User Guidance: Users receive clear instructions to remediate non-compliance, such as updating the OS or enabling encryption, minimising friction.
- Support for Multiple Platforms: Intune manages Windows, macOS, iOS, and Android devices, ensuring consistent security across your environment.
By enforcing device compliance with Intune, you ensure only healthy, trusted devices can access your organisation’s resources wherever your users are working.
Why Device Security is Essential in Zero Trust
Devices are the bridge between your users and your data. If a device is compromised, so is your environment regardless of how strong your identity controls may be. Attackers often target endpoints as the quickest route to stealing credentials, bypassing security controls, or launching ransomware.
Unmanaged or non-compliant devices present a major risk. With the rise of hybrid work and BYOD, the diversity and number of endpoints has exploded, making it even more challenging to maintain visibility and control.
Device health and compliance signals are now critical inputs for Conditional Access decisions. It’s not enough to know who is requesting access, you must also know the state of the device they’re using. Only by continuously verifying both identity and device health can you truly enforce Zero Trust principles and protect your organisation’s resources.
Real-world example:
Imagine a user tries to access SharePoint from an unmanaged device, perhaps a personal laptop that hasn’t been enrolled or checked for compliance. With Conditional Access in place, the user is allowed web-only access but is blocked from downloading files. This simple policy prevents sensitive data from being saved to an untrusted device, reducing the risk of data leakage if that device is lost, stolen, or compromised
Core Principles for Device Security
Before any device is granted access to your organisation’s resources, it must meet strict security standards, every single time. This is the heart of Zero Trust: never assume a device is safe and always validate its health and compliance. By following these core principles, you dramatically reduce the risk of attackers exploiting weak or unmanaged endpoints.
Managed vs Unmanaged Devices: Why It Matters
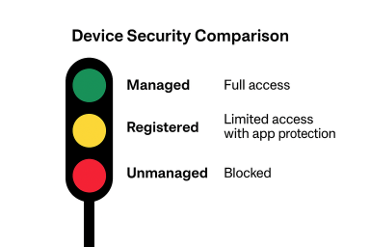
Not all devices are equal when it comes to security and compliance. In a Zero Trust model, you must distinguish between:
Corporate-Owned Devices (Managed):
- Fully enrolled in Intune, configured to meet all compliance requirements, and onboarded to Defender for Endpoint.
- These devices can be trusted to access sensitive resources, as they are visible, manageable, and protected by your organisation’s policies.
Personal-Owned Devices (Registered/Managed):
- User-owned but registered (or enrolled) with Intune.
- If fully enrolled, they can be managed and protected similarly to corporate devices – but this is a decision that should not be taken lightly.
- If only registered (not enrolled), they cannot be managed at the device level—Defender for Endpoint cannot be deployed, and compliance cannot be enforced. However, app protection policies can be applied to supported apps, protecting corporate data within the app container.
Personal-Owned Devices (Unmanaged):
- Not enrolled or registered with Intune, and not onboarded to Defender for Endpoint.
- These devices are invisible to your security team and cannot be trusted. No compliance or risk signals are available, and only basic app-level controls (such as web-only access and blocking downloads) can be enforced.
Best Practice:
Unmanaged personal devices should not be used to access organisational resources. Block access entirely wherever possible. Allowing access from such devices introduces significant risk, as there is no visibility, control, or ability to respond to threats.
Recommendation:
Require all personal devices to be at least registered with Intune or Entra before granting any access. For sensitive data require full enrolment and compliance. And for privileged roles require a PAW.
Why Block Unmanaged Devices?
Unmanaged devices represent a significant risk:
- They may be out of date, infected with malware, or have no security controls in place.
- You cannot enforce compliance, deploy Defender for Endpoint, or receive risk signals.
- Sensitive data could be downloaded or leaked without your knowledge.
Best Practice:
- Block unmanaged devices from accessing corporate resources entirely, or restrict them to web-only access with no downloads.
- Require anyone using BYOD to at least register their device with Intune. For access to sensitive data or privileged roles, require full enrolment and compliance.
Key Point:
- If it’s not managed, it’s not trusted. Make this clear in your policies and user communications.
Never trust by default
Zero Trust means exactly that, trust no device by default, regardless of whether it’s managed, unmanaged, corporate-owned, or personal. Every device must continuously prove it meets your organisation’s security standards before being granted access to sensitive resources. This approach helps prevent attackers from exploiting a single weak link in your device estate.
Example:
A contractor’s laptop, even if previously used for legitimate work, must still pass compliance checks every time it attempts to access company data. If the device falls out of compliance perhaps due to a missing security update or disabled encryption access is immediately restricted until the issue is resolved.
Continuous validation
Device health and compliance aren’t static. A device that was compliant yesterday could become a risk today due to malware, outdated software, or a change in ownership. Zero Trust requires that you validate device status at every access attempt, not just at the point of enrolment.
Example:
An employee’s mobile phone is enrolled and compliant but later becomes jailbroken or infected with malware. With continuous validation in place, Conditional Access policies will detect the change and block access to corporate resources until the device is remediated.
Why this matters:
Attackers are constantly looking for ways to exploit gaps in device security. By enforcing these core principles, you ensure that only healthy, trusted devices can access your environment reducing the risk of data breaches, ransomware, and credential theft.
The Microsoft Approach – Intune, Defender, and Compliance
Microsoft’s Zero Trust device strategy is built on a trio of integrated solutions Intune, Defender for Endpoint, and Conditional Access. Together, they provide a comprehensive framework for managing, securing, and controlling access from every device in your environment.
Microsoft Intune
Intune is the cornerstone of device management in a modern organisation. It enables you to enrol devices, corporate-owned or BYOD and apply configuration profiles, enforce compliance policies, and protect organisational data through app protection policies.
With Intune, you can:
- Ensure all devices meet your minimum security standards before accessing resources.
- Automate patching, configuration, and policy enforcement across Windows, macOS, iOS, and Android.
- Apply app protection policies to secure data on personal devices without taking over the entire device.
- Gain visibility into your device estate with real-time compliance dashboards and reporting.
Microsoft Defender for Endpoint
Defender for Endpoint provides advanced threat protection for every device, going beyond traditional antivirus. It delivers:
- Real-time detection and response to threats such as malware, ransomware, and zero-day exploits.
- Attack surface reduction, helping to minimise the ways attackers can compromise devices.
- Endpoint detection and response (EDR), giving security teams the tools to investigate and remediate incidents quickly.
- Integration with Intune, so device risk signals can automatically influence access decisions.
Conditional Access
Conditional Access is the policy engine that brings it all together. By using device compliance as a condition for access, you can:
- Block or restrict access from non-compliant or unmanaged devices, ensuring only healthy endpoints can reach sensitive apps and data.
- Apply granular controls, such as allowing web-only access or blocking downloads based on device health, user risk, or location.
- Continuously adapt to changing risk signals, automatically enforcing policies in real time.
In practice:
When a user attempts to access a corporate resource, Conditional Access evaluates both their identity and the health of their device. If the device is compliant and protected by Defender for Endpoint, access is granted. If not, access is blocked or restricted, and the user is guided to remediate any issues.
By combining Intune, Defender for Endpoint, and Conditional Access, you create a dynamic, adaptive security posture, one that continuously validates both users and devices, and only allows trusted endpoints to access your organisation’s most valuable data.
Practical Steps to Secure Devices
Securing devices in a Zero Trust model isn’t just about technology, it’s about building a layered, adaptable approach that covers every endpoint, user, and scenario. Here’s how to put these principles into practice:
Enrol and Manage All Corporate-Owned Devices
- Require enrolment for all corporate-owned devices this includes Windows, macOS, iOS, and Android. This ensures every device is visible, manageable, and compliant from day one.
- Use Intune for configuration, patching, and compliance. Automate updates and enforce security baselines to reduce vulnerabilities.
Register and Protect Personal Devices (BYOD)
- Require registration for personal devices (BYOD). Users should register their devices with Intune to gain access to corporate resources.
- Apply app protection policies to registered personal devices, especially for mobile. These policies protect corporate data within approved apps, without taking over the user’s entire device.
Define and Enforce Compliance Policies
- Set minimum OS versions, require encryption, and block jailbroken/rooted devices. These basic controls prevent outdated or compromised devices from becoming a weak link.
- Enforce Defender for Endpoint onboarding for advanced protection (managed devices only), ensuring every managed device benefits from real-time threat detection and response.
- Use compliance policies as a gate for Conditional Access. Only devices that meet your standards should be allowed to access sensitive resources.
Note:
Defender for Endpoint onboarding and device compliance policies can only be enforced on managed devices (Intune-enrolled or Hybrid Azure AD Joined). Personal devices that are only registered (not enrolled) cannot be onboarded to MDE or have device compliance policies applied; instead, rely on App Protection Policies and Conditional Access session controls for these endpoints.
Conditional Access: Only Allow Healthy Devices
- Block access from unmanaged or non-compliant devices to sensitive apps and data. This stops risky endpoints at the door.
- Allow limited access (e.g., web-only, no downloads) for personal devices if needed. This balances security with user productivity, especially in hybrid or remote work scenarios.
- Use device filters and authentication context for granular control. Tailor access policies based on device type, risk level, or user role.
Monitor, Detect, and Respond
- Use Defender for Endpoint for real-time threat detection and automated response. Quickly identify and contain threats before they spread.
- Integrate device risk signals into Conditional Access. For example, automatically block access if a device is flagged as high risk.
- Regularly review device inventory and compliance reports. Stay ahead of emerging risks by maintaining visibility across your entire device estate.
Empower Users and Support BYOD Securely
- Educate users on why device management matters. Clear communication helps drive adoption and reduces resistance.
- Make enrolment and compliance as frictionless as possible. Streamlined processes encourage users to stay compliant without frustration.
- Use app protection policies for personal devices. Protect corporate data within approved apps, allowing users to keep their personal information private.
By following these practical steps, you create a robust, adaptive defence that keeps your organisation’s data secure—no matter where or how your users work.
Sample Conditional Access Policies
The following sample policies illustrate practical approaches for managing access across a diverse device estate, including corporate-owned, BYOD computers, and BYOD mobile devices. Each policy is designed to balance security with user productivity, providing clear guidance on how to enforce registration, compliance, and app protection requirements for different device types.
Use these examples as a foundation for your own Conditional Access strategy, adapting them to meet the specific needs and risk profile of your organisation.
Corporate Device Access
Policy:
Allow full access to all corporate apps and resources from devices that are fully managed and compliant (Intune-enrolled or Hybrid Entra Joined).
How it works:
- Applies to all corporate-owned devices.
- Devices must be enrolled in Intune or Hybrid Azure AD Joined and meet compliance requirements (e.g., OS version, encryption, antivirus, Defender for Endpoint).
- Conditional Access grants full access to all corporate apps and resources (e.g., Outlook, OneDrive, SharePoint, Teams, etc.).
- No restrictions on downloads, clipboard, or print actions.
Effect:
- Ensures only trusted, compliant corporate devices have unrestricted access to organisational data and collaboration tools.
- Enables full productivity while maintaining robust security controls.
Best Practice:
Enforce regular compliance checks and automated remediation for managed devices.
Use Defender for Endpoint for real-time threat detection and response.
Review compliance dashboards regularly to maintain visibility and control.
Require Personal Devices to be Registered
Policy:
Allow access from personal (BYOD) devices only if they are registered with Intune or Azure AD.
How it works:
- Applies to all users or specific groups needing BYOD access.
- Conditional Access checks for device registration status.
- If the device is registered, access is allowed (with app protection/session controls); if not, access is blocked.
- Unregistered personal devices are denied access or restricted to web-only access with no downloads, clipboard, or print actions.
Effect:
- Ensures that even personal devices are at least visible to IT and can be subject to app-level controls.
- App protection policies can be applied to supported apps (e.g., Outlook, Teams, OneDrive) on registered devices.
- These policies protect corporate data within the app container (e.g., require PIN, block copy/paste, prevent data backup), but do not manage the device itself.
Best Practice:
- Block unmanaged/unregistered devices entirely, or restrict them to web-only access with no downloads.
- Require all BYOD users to at least register their device for app protection policies.
- For access to sensitive data or privileged roles, require full enrolment and compliance.
Block Legacy Authentication
Policy:
Block all legacy authentication protocols (POP, IMAP, SMTP Basic Auth) that do not support modern security controls.
Target:
All cloud apps.
Effect:
Reduces risk from outdated protocols that are often targeted by attackers.
Restrict BYOD Access to Web-Only (Computers)
Policy:
Restrict service access from personal (BYOD) computers to web-only (browser) sessions.
How it works:
- Applies to personal (BYOD) computers.
- Conditional Access restricts access to Teams, Outlook, SharePoint etc… to web-only (browser) sessions.
- App-enforced restrictions: No downloads, clipboard, or print actions permitted.
Effect:
Protects sensitive data by preventing downloads or local storage on unmanaged personal computers.
BYOD Mobile Devices – Registration and App Protection Only
Policy:
Allow Teams access from personal (BYOD) mobile devices only if they are registered and enforce App Protection Policies.
How it works:
- Applies to personal (BYOD) mobile devices (iOS/Android).
- Devices must be registered with Azure AD or Intune.
- Access to services permitted only via approved mobile apps (e.g., Teams/Outlook mobile app) with App Protection Policies enforced.
- App Protection Policies: Require PIN, block copy/paste, prevent backup, and restrict data sharing outside the app.
Effect:
Corporate data is protected within the app container; device itself is not managed.
Summary Table: Conditional Access Policies for All Apps
| Device Type | Registration Required | Compliance Policies | App Protection Policies | Access Type | Restrictions |
| Corporate-Owned (Managed/Enrolled) | Yes | Yes | Yes | Full (desktop & app) | None |
| BYOD Computer (Registered) | Yes | No | Yes (if supported) | Web-only | No downloads, clipboard, print |
| BYOD Computer (Unmanaged) | Blocked | N/A | N/A | Blocked | No access |
| BYOD Mobile (Registered Only) | Yes | No | Yes | Mobile app only | App container only, no device mgmt |
| BYOD Mobile (Unmanaged) | Blocked | N/A | N/A | Blocked | No access |
Notes:
- App Protection Policies include controls such as requiring PIN, blocking copy/paste, preventing backup, and restricting data sharing outside the app.
- Web-only access restricts downloads, clipboard, and print actions to protect corporate data on unmanaged or personal computers.
- Mobile app only access ensures corporate data is protected within the app container on registered BYOD mobiles.
Restrict Privileged Roles to Privileged Access Workstations (PAWs)
Privileged accounts—such as Global Admins—are prime targets for attackers. The most effective way to protect these accounts is to ensure that privileged operations can only be performed from a tightly controlled set of dedicated, hardened devices: Privileged Access Workstations (PAWs). This approach dramatically reduces the risk of credential theft, malware, or lateral movement from compromised endpoints.
To enforce this, use two layered Conditional Access policies:
Policy 1: Require Phishing-Resistant MFA for Privileged Roles
- Purpose: Ensure that all users in privileged roles must authenticate using phishing-resistant multi-factor authentication (MFA), such as FIDO2 security keys, certificate-based authentication, or Windows Hello for Business.
- How to configure:
- Assign to privileged roles (e.g., Global Admin, Privileged Role Admin).
- Grant control: Require authentication strength set to “Phishing-resistant MFA”.
- Applies everywhere, regardless of device.
- Effect: Even if credentials are compromised, attackers cannot access privileged roles without a strong, phishing-resistant second factor.
Policy 2: Restrict Privileged Access to PAWs
- Purpose: Block privileged role sign-in from any device except those explicitly identified as PAWs.
- How to configure:
- Assign to the same privileged roles.
- Use device filters or device groups in Conditional Access to specify which devices are permitted (e.g., filter by device name, tag, or compliance state).
- Exclude “Break Glass” accounts if necessary, but ensure these are closely monitored and protected.
- Effect: Only pre-approved, highly secure PAWs can be used for privileged operations. Admins cannot perform sensitive actions from their day-to-day or personal devices.
Why this matters:
By combining these two policies, you enforce true Zero Trust for privileged operations. Even if an attacker obtains credentials, they cannot escalate privileges or access admin portals without both a PAW and phishing-resistant authentication.
Monitoring Personal Devices in a Zero Trust Model
App Protection Policies (APP)
- For personal devices (BYOD) that are registered but not managed, you cannot deploy MDE or enforce device compliance policies.
- Instead, use App Protection Policies (APP) via Intune to protect corporate data within supported apps (e.g., Outlook, Teams, OneDrive).
- APP can enforce requirements such as PIN, block copy/paste, prevent backup, and restrict data sharing outside the app container.
- These policies provide visibility into app-level activity and can trigger actions (e.g., wipe corporate data from the app if risk is detected).
Conditional Access Session Controls
- Use Conditional Access to restrict access from personal devices to web-only or app-only, with session controls that block downloads, clipboard, and print actions.
- Session controls can limit exposure of sensitive data and reduce the risk of data leakage from unmanaged endpoints.
Monitoring and Reporting
While you cannot monitor the device itself, you can monitor:
- Sign-in activity: Use Entra ID sign-in logs to track access attempts from personal devices.
- App activity: Review usage and compliance reports for apps protected by APP.
- Access reviews: Regularly review who is accessing sensitive resources from personal devices, especially in high-risk groups.
4. Automated Response
- If suspicious activity is detected (e.g., unusual sign-in patterns, policy violations within protected apps), Conditional Access can automatically block access or require re-authentication.
- Intune can trigger selective wipe of corporate data from the app if the device falls out of compliance with APP.
User Education and Support
- Educate users on the importance of registering their personal devices and complying with app protection requirements.
- Provide clear guidance on how to remediate issues (e.g., update app, enable PIN, re-register device).
Limitations:
- You cannot monitor device health, malware status, or compliance signals on personal devices that are only registered.
- Security controls are limited to the app container; the device itself remains outside IT management.
Best Practice:
- For access to sensitive data or privileged roles, require full device enrolment and compliance (so MDE and full monitoring can be enforced).
- For general access, rely on app protection and session controls to minimise risk.
How to Monitor, Detect, and Respond
Enforcing policies is only part of the story, continuous monitoring and rapid response are essential for effective Zero Trust.
Real-Time Threat Detection
- Defender for Endpoint: Provides real-time detection and automated response to threats such as malware, ransomware, and suspicious activity on devices.
- Exploit Guard & Attack Surface Reduction: Reduces the ways attackers can compromise devices by enforcing strict security controls.
Integrate Device Risk Signals
- Conditional Access Integration: Device risk signals from Defender for Endpoint can automatically influence access decisions (e.g., block access if a device is flagged as high risk).
- Session Controls: Apply restrictions such as blocking downloads, clipboard actions, or print operations from unmanaged devices.
Regular Review and Reporting
- Compliance Dashboards: Use Intune and Entra dashboards to monitor device compliance status across your estate.
- Sign-In Logs and Sentinel: Monitor Entra sign-in logs and integrate with Microsoft Sentinel to detect anomalies, policy bypass attempts, and suspicious activity.
- Access Reviews: Regularly review who has access to sensitive resources, especially in high-risk groups or privileged roles.
Automated and Manual Response
- Automated Response: Configure automated actions in Defender and Sentinel to isolate compromised devices, disable accounts, or trigger access reviews.
- Manual Response: Security teams should investigate alerts, review incident details, and take remediation actions as needed.
Continuous Improvement
- Test in Report-Only Mode: Validate new CA policies before enforcement to avoid accidental lockouts.
- Audit and Learn: Continuously validate that policies are working, adapt to new threats, and feed lessons learned back into your security strategy.
Example in Practice:
A user attempts to access SharePoint from an unmanaged device. Conditional Access blocks downloads and allows web-only access, preventing sensitive data from being saved to an untrusted endpoint. If Defender for Endpoint detects malware on a device, access is immediately blocked, and the security team is alerted for investigation
Common Pitfalls and How to Avoid Them
- Relying on device registration alone, enforce compliance, not just registration.
- Ignoring personal devices, use app protection and Conditional Access to manage risk.
- Overly restrictive policies, balance security with user productivity.
Resources and Further Reading
- https://docs.microsoft.com/en-us/mem/intune/
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/
- https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/
- Recommended blog: https://www.welkasworld.com/ for Conditional Access and device policy best practices.
Conclusion
Devices are the frontline of Zero Trust, every device is a potential entry point. By combining management, compliance, and real-time risk signals, you can ensure only trusted devices access your data.
Next up: Applications – the third pillar.
Was this helpful?
Let me know what you think!