
Table of Contents
Introduction
I’ve been working with a customer recently assisting with sorting out their privileged access and assisting them with their adoption of PIM (Privileged Identity Manager)
Whilst I’d argue that PIM is not essential to secure you access to Entra, it is, in my view good practice and reduces the attack surface. You can use the likes of Conditional Access to block access to any privileged role from un trusted devices etc regardless of using PIM but the two combined make it that more secure.
In my view security is not complicated, it’s common sense and you doing the most you can to prevent any breach. Privileged accounts should be treated the same. There is no one right way to protect them, but there are a few ways that maybe you should re-evaluate.
What is an Entra privileged role
Let’s see what copilot say an Entra privileged role is:
In Microsoft Entra ID, privileged roles are specific roles and permissions that allow users to manage directory resources, modify credentials, authentication or authorization policies, and access restricted data. These roles are essential for delegating administrative tasks, but it’s crucial to use them securely.
So Global Administrator, for sure is a privileged role, a highly privileged role. I would also say all service admins are too.
Well, Microsoft label roles that are privileged in Entra:
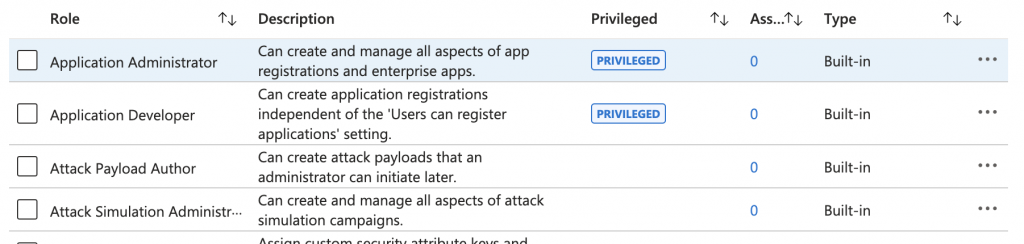
However, I’d say that Microsoft in this case have missed out more than a few roles that I would call Privileged.
- Exchange Administrator
- SharePoint Administrator
- Teams Administrator
These are to name but a few. Maybe I am over complicating things, or missing something but I would say those are all very much privileged roles that have the ability to do some damage if used in the wrong way.
So, I would say, there are 3 levels of access, Top (Global Administrator) Middle (Service Admins and anything marked privileged) and Bottom (all other roles).
Tiering Model
Both Microsoft and the NCSC recommend using a Tiering model for your access
They both follow the principal of least privilege. Which, is easier to use when you have something like PIM for your admin accounts.
The Top, Middle, And Botton levels of Entra Roles falls in nicely with the Tiering model
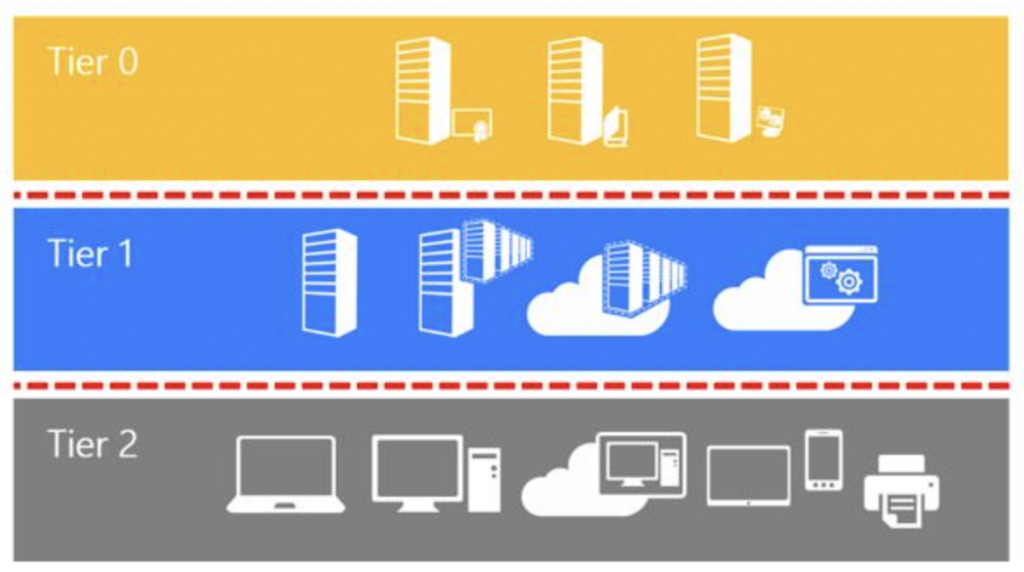
This image is from: Securing privileged access Enterprise access model – Privileged access | Microsoft Learn. While this is aimed at on-premises I’d say the principle still applies to the cloud. I would translate this as Top is Tier 0, Middle is Tier 1 and Bottom is Tier 2
Which would break the Entra Roles up in the following way:
| Tier 0 | Tier 1 | Tier 2 |
| Global Admin | Application Administrator Application Developer Authentication Administrator Authentication Extensibility Administrator B2C IEF Keyset Administrator Cloud Application Administrator Cloud Device Administrator Conditional Access Administrator Directory Writers Domain Name Administrator External Identity Provider Administrator Global Reader Helpdesk Administrator Hybrid Identity Administrator Intune Administrator Lifecycle Workflows Administrator Password Administrator Privileged Authentication Administrator Privileged Role Administrator Security Administrator Security Operator Security Reader User Administrator Teams Administrator SharePoint Administrator Exchange Administrator Windows 365 Administrator Windows Update Deployment Administrator Yammer Administrator Authentication Policy Administrator Azure DevOps Administrator Cloud App Security Administrator Dynamics 365 Administrator Fabric Administrator Attack Simulation Administrator Attribute Assignment Administrator Attribute Log Administrator Compliance Administrator Customer LockBox Access Approver Global Secure Access Administrator Identity Governance Administrator Power Platform Administrator Teams Telephony Administrator Teams Devices Administrator Teams Communications Administrator Groups Administrator | Attribute Assignment Reader Attribute Definition Administrator Attribute Definition Reader Attribute Log Reader Azure Information Protection Administrator B2C IEF Policy Administrator Billing Administrator Compliance Data Administrator Desktop Analytics Administrator Directory Readers Dynamics 365 Business Central Administrator Edge Administrator Exchange Recipient Administrator Extended Directory User Administrator External ID User Flow Administrator External ID User Flow Attribute Administrator Guest Inviter Insights Administrator Insights Analyst Insights Business Leader Kaizala Administrator Knowledge Administrator Knowledge Manager License Administrator Message Center Privacy Reader Message Center Reader Microsoft 365 Migration Administrator Microsoft Entra Joined Device Local Administrator Microsoft Hardware Warranty Administrator Microsoft Hardware Warranty Specialist Network Administrator Office Apps Administrator Organizational Branding Administrator Organizational Messages Approver Organizational Messages Writer Permissions Management Administrator Printer Administrator Printer Technician Reports Reader Search Administrator Search Editor Service Support Administrator SharePoint Embedded Administrator Skype for Business Administrator Teams Communications Support Engineer Teams Communications Support Specialist Tenant Creator Usage Summary Reports Reader User Experience Success Manager Virtual Visits Administrator Viva Goals Administrator Viva Pulse Administrator |
Once you have your tiers defined and if you’re using PIM you’d then want to look at how long each tier can be activated for. By default any role can be activated for a duration of 8 hours. I’ve found this more than adequate, basically a working day.
Access Reviews
If you’ve got access to Entra ID P2 Licenses, and using PIM you can also look at using Access Reviews. These will trigger reviews on a set schedule for users with the role and require an action. Then, depending on the action the user keeps the role or the role is removed.
The next question would be, how long should a user be eligible to activate a role? this comes down to your own requirements. There is no set in stone review time so I’ve gone with a bit of common sense here.
I’d say that its prudent to review Tier 0 every 3 Months, Tier 1 and 2 I’d say review every 6 months. If you are using PIM then there is also the ability to only allow admins to be eligible for set period of time, however I’d say this is only for specific cases. My argument is you’ve employed someone to do a job so you trust them with the role, you’d not want to put that kind of limit on it.
Conclusion
So my view of this is the following. This is only my opinion and interpretation of the recommendations that are out there.
Follow the principle of least privileged, this is always recommended. Don’t always just hand out the easiest role to an admin, that is usually more than often the Global Administrator role (we’ve all done it in the past).
Separate the roles as best you can. This shouldn’t be complicated. At the end of the day use your common sense with your privileged roles. Follow some of the guidance available online from Microsoft, NCSC and other Government Cyber Security recommendations.
When creating your privileged accounts use a separate cloud only account from the users everyday account, and assign them a Microsoft Entra P2 License, this will provide them with the best level of protection. In all honesty I am unsure if you need or don’t need to assign the privileged account a licensing if their everyday user account has one, this is a grey area, so my view is if in doubt assign a license, purchase one if you do not have any for the. The cost of the license is worth it in the long run.
Do privileged accounts need a mailbox? My answer is no, I don’t think they do, lets face it, if you’re using separate accounts you’d more than likely not check the mailbox of it anyway. My recommendation is to create the accounts as Mail Enabled Users with an external address of the users regular mailbox. this will mean they get emails sent to the privileged account.
Use the tools available to you, and phase them in gradually, you do not need to do it all at once.
Keep the number of Global Admin’s to a minimum. Whilst Microsoft recommend no more than 5, use common sense. But make all the Global Admins Eligible for the role and not permanently active.
The only privileged accounts in Entra with a permanent active assignment should be your two break glass accounts.